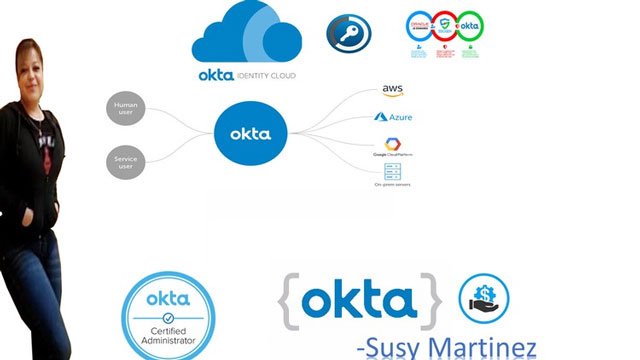
API Developer (Python/Django Rest/Flask/PostgreSQL/Postman)

Demo : API Developer (Python/Django Rest/Flask/PostgreSQL/Postman)
An API is a set of definitions and protocols for building and integrating application software. It’s sometimes referred to as a contract between an information provider and an information user—establishing the content required from the consumer (the call) and the content required by the producer (the response).