Writing Secure Code in Node.js Path – Part2
Demo : Writing Secure Code in Node.js Path – Part2
Node.js is the most popular server-side asynchronous runtime. Applications built with this technology heavily depend on the npm ecosystem.
Node.js is the most popular server-side asynchronous runtime. Applications built with this technology heavily depend on the npm ecosystem.
Demo: Writing Secure Code in Node.js Path – Part1
Node.js is the most popular server-side asynchronous runtime. Applications built with this technology heavily depend on the npm ecosystem.

This IoT Security training is designed to help IT professionals strengthen their knowledge about the Internet of Things (IoT) and the security platforms related to it. You’ll also be able to identify the security, privacy and safety concerns related to the implementation of an IoT infras

Pentesting is much like taking a battering ram to the door of a fortress. You keep pounding away but try to find a secret backdoor to enter through. But what happens if pieces of the network are outside the fortress? The solution to this problem is IOT pentesting.

The eLearnSecurity Network Defense Professional (eNDP) certification is issued to security engineers that provide proof of their hands-on skills through a comprehensive practical exam.


Certified Information Systems Security Professional (CISSP) verifies one has mastery of a multitude of information security and cybersecurity topics, something that’s necessary for information security management and leadership (a job that many CISSP holders fulfill). Our online CISSP training covers topics ranging from operations security, telecommunications, network and internet security, identity and access management systems and methodology, and business continuity planning.
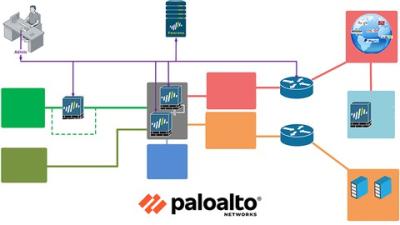
Welcome to Palo Alto PCNSE with the Panorama NextGen Firewall training program *Videos only)
“Palo Alto is an industry leader in the next-gen Firewall”. The course covers the
Palo Alto Firewall “basis to advance”, concepts in a most practical way ensuring that delegates not only pass the exam but are also ready for a real-world environment.

File Size1.78 GB
In an increasingly connected world, Identity and Access Management is critical to securing the access and availability of enterprise assets. Effective IAM ensures that the right people have access to the right assets.

File Size6.95 GB
The Palo Alto Networks Certified Network Security Administrator certification is designed not only for security professionals, but customers, value added resellers, pre-sale systems engineers, system integrators and system administrators too.
Demo : Software Security Testing
File Size2.13 GB
Software security testing offers the promise of improved IT risk management for the enterprise. By testing for flaws in software, security testing solutions seek to remove vulnerabilities before software is purchased or deployed and before the flaws can be exploited.

File Size1.98 GB
With the growing need for cybersecurity across the world, developers who have mastered cyber resilience get ahead. Secure coding in ASP.NET is an instrumental pathway for all developers who wish to build secure and cyber-resilient software.
File Size1.62 GB
Azure Active Directory (Azure AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services. Initially, Active Directory was used only for centralized domain management

File Size1.00 GB
Software Security is one of the most important aspects of Software Architecture these days.

Demo : React Security: Best Practices
File Size6.31 MB
Users expect Web applications to be secure and React apps are no different. In this course, React Security: Best Practices, you’ll learn to improve the security of your React applications.

File Size1 GB
you will learn how to use advanced FortiGate networking and security. Topics include features commonly applied in complex or larger enterprise or MSSP networks, such as advanced routing, transparent mode, redundant infrastructure, site-to-site IPsec VPN, single sign-on FortiOS 7.0 Formats l Instructor-led classroom l Instructor-led online l Self-paced online

File Size690 MB
OpenVAS/GVM is a fully-featured vulnerability scanner, but it’s also one component of the larger “Greenbone Security Manager” (GSM).

Prepare for the CertNexus Certified IoT Security Practitioner Exam

File Size625.8 MB
Hello everyone! I hope you are doing great.
Have you ever thought of going for IT or Security related exams in your whole life?! I am sure you did! We always want to develop our skills and certification is one of the finest ways to do it!

File Size2.8 GB
Movement, Pivoting, and Persistence for Pentesters and Ethical Hackers is the next step in YOUR penetration testing and ethical hacking journey.